Archives: Projects
Projects

My Path to DevOps

From NYPD Sergeant to DevOps Engineer
My Self-Taught Journey into Cloud & Automation
After retiring from the NYPD and serving in the U.S. Army, I set out to build my next chapter — not in uniform, but in the terminal. What began as simple curiosity about Linux quickly evolved into a passion for DevOps, infrastructure, and automation. Over the past year, I’ve transformed my homelab into a production-grade environment — and now I’m applying those skills in the professional world.Timeline of My DevOps Journey
🔹 December 2024 — The Spark of Virtualization
Installed Linux on an Intel N100 mini PC, which opened the door to system-level thinking and automation. Soon after, deployed a Plex Media Server in Docker, mounted a 16 TB Synology NAS, and began exploring VPN access and virtualization — marking the true beginning of my homelab journey.🔹 January 2025 — Dynamic DNS & Security+ Certified
Set up Dynamic DNS using Cloudflare’s API, Bash, and cron — my first real step into Infrastructure as Code and network automation. Also earned my CompTIA Security+ certification, marking the start of my deep dive into cybersecurity fundamentals.🔹 February — Lightweight Observability
Wrote custom Bash scripts to track system health (CPU, memory, disk, SSH attempts) and emailed daily summaries. This became my introduction to observability and alerting.🔹 March — Cloud Database Training
Completed Google Cloud’s 70-hour Database Engineer learning path, covering:- Cloud SQL
- Spanner
- Bigtable
- AlloyDB
- Migration strategies & resiliency patterns
🔹 April — Tooling & Productivity
Sharpened my daily drivers: Git, GitHub, Docker, and tmux. Learned to manage containers, adopt version control workflows, and automate repeatable tasks via CLI.🔹 May — Full Stack Infrastructure + CI/CD + Security + Cloud Deployment
Everything started to come together into a secure, automated stack:- Reverse-proxied services via Docker, Traefik, Cloudflare, and Let’s Encrypt TLS
- Deployed a public-facing NGINX site on AWS EC2 with DNS, UFW firewall, and automated TLS
- Built a CI/CD pipeline with GitHub Actions for Dockerized apps, deployed over SSH
- Hardened SSH with key-only login, Fail2Ban, and daily intrusion reports
🔹 June — Internship Kickoff, GCP IAM & SSH Certificate Automation
June marked the start of my DevOps internship at Rakuten Advertising, focused on securing and scaling cloud infrastructure. Key milestones:- Managed IAM roles and PAM integrations in GCP to enforce time-bound access
- Earned the Google Associate Cloud Engineer certification
- Deployed SSH certificate-based authentication via HashiCorp Vault in my homelab
🔹 July — IAM to PAM Automation, Mentorship & App-Backed Database
Built a script to convert IAM roles into PAM-managed entitlements, reducing privilege windows and enforcing least privilege. Also built a MySQL-backed app for internal tooling — sharpening infrastructure and automation skills. Most importantly, I learned from a phenomenal team of seasoned DevOps engineers, gaining invaluable mentorship in real-world DevSecOps.🔹 August — Event-Driven PAM Alerts & Terraform Rollout
Engineered an event-driven alert system to improve visibility into PAM approvals:- Slack notifications for instant visibility
- SendGrid email confirmations
- Full Terraform rollout for reproducible deployments
🔹 September — Load Balancers, CDN Optimization & Balancing College Life
Continued contributing to Rakuten’s DevOps team by tackling Jira tickets on load balancers, CDN optimizations, and performance monitoring — strengthening my grasp of traffic management and failover mechanisms. At the same time, I returned to full-time classes at Farmingdale State College, studying:- Cisco Networking — routing, switching, and design
- Operating Systems — process and memory management
- Vulnerability Analysis — bridging DevOps with cybersecurity
🔹 October — Wrapping Up an Incredible Internship & Strengthening My Security Foundations
As my seven-month internship at Rakuten Advertising concludes, I’m deeply grateful for the experience. These months gave me hands-on exposure to cloud automation, IAM/PAM security, and real-world DevSecOps — turning knowledge into production-ready skills. To close this chapter, I completed the HashiCorp Certified Vault Associate course, deepening my understanding of secrets management, dynamic credentials, and policy-based access. Meanwhile, I continue full-time studies in Networking, Operating Systems, and Vulnerability Analysis, reinforcing everything I’ve built through my internship and homelab work. October has been about reflection, certification, and momentum — closing one chapter and preparing for the next phase of my DevOps journey.🔹 November — Finishing the Semester & Going All-In on CCNA Prep
As fall winds down, November is all about closing out my college semester strong while doubling down on networking fundamentals. I’m working through the full 63-day Jeremy’s IT Lab CCNA course on Udemy — dedicating the entire month to routing, switching, STP, VLANs, OSPF, EtherChannel, WAN technologies, and packet-flow analysis. My goal: Complete the full course in November so I can sit for the CCNA exam in December. Between labs in Packet Tracer, subnetting drills, and hands-on practice with STP root configuration, HSRP, DHCP relay, and OSPF, this month bridges everything I’m learning in college with everything I’ve built in my homelab and during my internship. It’s the perfect way to wrap up 2025 — ending the year with momentum, mastery, and a major certification goal in sight.🔹 December — CCNA Certified, Automated Proxmox VM Provisioning & Centralized Logging
After weeks of labs, subnetting drills, and late-night study sessions, I passed the Cisco Certified Network Associate (CCNA) exam — strengthening my networking foundation alongside my systems and DevOps skillset. I also completed the fall semester at Farmingdale State College with a 3.95 GPA, entering my final two semesters before graduation. This month marked a major milestone: implementing Terraform- and Jenkins-driven Proxmox VM provisioning and deploying centralized monitoring and logging with Grafana and Loki, transitioning my homelab from manual builds to fully automated, observable, and reproducible infrastructure.Tooling Overview
- Infrastructure & Virtualization - Proxmox VE (MinisForum MS-01) · Terraform · Cloud-Init
- Automation & Configuration Management - Ansible · Jenkins · GitHub Actions · cron
- Networking, Proxy & DNS - Docker · Traefik · Cloudflare DNS
- Monitoring & Observability - Prometheus · Node Exporter · Grafana · Loki · Promtail
- Security & Access Control - HashiCorp Vault · SSH certificate authentication · UFW · Fail2Ban · Let’s Encrypt TLS
- Cloud & Hosting - AWS EC2 · NGINX (Alpine) · GCP IAM
Key Highlights
- Automated Proxmox VM lifecycle management using Terraform and Jenkins, enabling repeatable VM creation triggered from GitHub commits
- Standardized system builds with cloud-init templates for users, SSH access, networking, and baseline configuration
- Post-provisioning system configuration and hardening using Ansible for packages, services, and security controls
- End-to-end automation workflow: GitHub → Jenkins → Terraform → Proxmox → Ansible
- Implemented automatic TLS certificate issuance and renewal using Traefik and Let’s Encrypt
- Deployed and secured AWS-hosted NGINX services behind Cloudflare DNS with firewall controls
- Built real-time monitoring and logging dashboards with Grafana, Prometheus, and Loki for system health and troubleshooting
- Implemented short-lived SSH certificate authentication via HashiCorp Vault for auditable, least-privilege access
- Generated daily SSH intrusion and Geo-IP reports to support security monitoring and incident awareness
Final Thoughts
Systems administration brings the structure, discipline, and operational ownership I developed through military and public service — with the added challenge of continuous learning. My homelab was the proving ground. Now, I’m supporting and operating systems in production.Let’s Connect
GitHub Projects LinkedIn Thanks for reading — feel free to connect or share your own DevOps journey!
Proxmox VM Decommissioning Pipeline
Plex Server
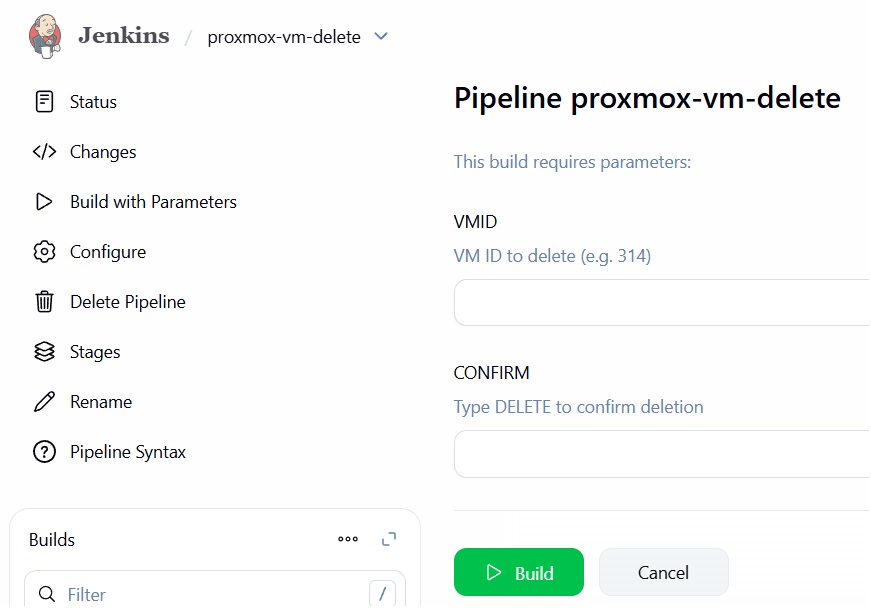
Proxmox VM Decommissioning Pipeline with Jenkins (Safe Infrastructure Teardown)
I built an automated, safety-first VM decommissioning pipeline for Proxmox VE using Jenkins CI/CD and the Proxmox REST API. This project focuses on responsibly automating destructive infrastructure actions while enforcing guardrails, dependency cleanup, and audit-friendly workflows.
The pipeline demonstrates how infrastructure teardown should be treated as a controlled, intentional process — not an ad-hoc manual task.
All hosts, IPs, paths, and credentials are redacted for safe public sharing.
Tech Stack
- Jenkins - Declarative CI/CD pipeline for controlled execution
- Proxmox VE REST API - API-driven VM lifecycle management
- Bash and Python - Validation logic and API orchestration
- Prometheus with Docker Compose - Monitoring dependency cleanup
- SSH = Remote configuration management
- jq -Safe JSON parsing and validation
Pipeline Flow Overview
Jenkins Job (Manual Execution)
- Pipeline must be manually triggered
- Designed to prevent accidental execution
Input Validation and Guardrails
- VMID must be numeric
- VMID checked against protected ranges
- CONFIRM=DELETE parameter required to proceed
- Pipeline aborts immediately on validation failure
Prometheus Dependency Cleanup
- SSH into monitoring host
- Remove VM’s Node Exporter IP from a clearly defined managed block in prometheus.yml
- Preserve all unmanaged configuration
- Restart Prometheus safely to apply changes
Proxmox API Shutdown
- Issue graceful shutdown request
- Wait with timeout enforcement
- Force stop only if required
Proxmox API Deletion
- Delete VM via API
- Purge attached disks
- Ensure no orphaned resources remain
Prometheus Target Management
Before VM deletion, the pipeline removes the VM’s monitoring target from Prometheus to ensure observability remains accurate and clean.
This prevents:
- Stale scrape targets
- False alerts and alert fatigue
- Configuration drift
- Accidental Prometheus config corruption
Only explicitly managed entries are modified; all other Prometheus configuration remains untouched.
Security and Safety Model
- Manual pipeline execution required
- Explicit confirmation flag for destructive actions
- Protected VMID ranges enforced
- API-driven actions with no CLI scraping
- Secrets injected via Jenkins Credentials
- No credentials committed to Git
- Clear separation of code, config, and secrets
What This Project Demonstrates
- Safe automation of destructive infrastructure tasks
- Dependency-aware decommissioning workflows
- CI/CD-controlled “kill paths”
- API-first infrastructure lifecycle management
- Enterprise-grade guardrails for production environments
This pipeline reflects real-world expectations for regulated, defense, or high-availability environments where automation must be both powerful and safe.
Use Case
Portfolio-grade example suitable for:
- DevOps Engineer roles
- Infrastructure / Platform Engineering
- Systems Administration
- Regulated or defense-sector environments
- CI/CD pipeline design and safety reviews
Repository
GitHub: https://github.com/mikecozier/proxmox-terraform-ansible-jenkins-delete-vm